8 Things You Need to Do Immediately to Protect Your Business
Did you know that Australia is currently the target of a focused and unrelenting cyberattack from a sophisticated foreign entity? No matter how big or small your business is, this vital information means one thing: you need to act now to protect yourself.
Who is Being Targeted?
Short answer: Every Australian including businesses, Government organisations and private citizens.
Nobody is immune to the tactics being used and everyone’s private data is seen as desirable. It’s not just credit card numbers, bank details, usernames and passwords, all of your personal and business data has a value on the dark web. Economists say data is worth more than gold or oil in today’s economy.
In the Last 12 Months…
- 51% of businesses attacked by ransomware
- 58% saw increase in phishing attacks
- 60% increase in impersonation fraud
- 82% experienced downtime from an attack
What Can You Do?
The Federal Government’s Australian Cyber Security Centre (ACSC) says it’s imperative that you are alert to this threat and take steps now to enhance the resilience of your computer networks and smart technology.
8 Things You Need to Do Immediately to Protect Your Business
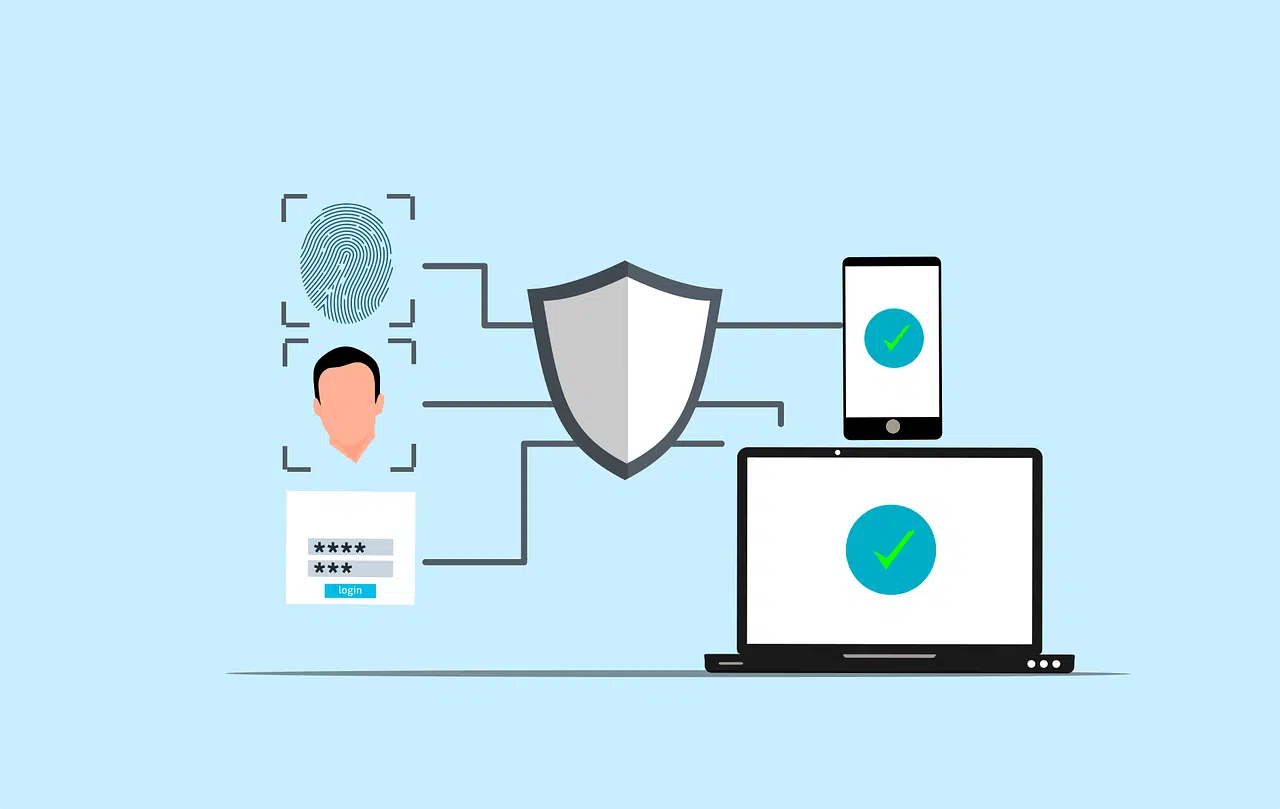
1. Multi-factor authentication (MFA)
You may already be using multi-factor authentication for some of your accounts. If you’re not, you need to start using it right away on all accounts. It’s hands down one of the most effective ways to protect your systems from cybercriminals.
MFA requires you or your staff to input a username and password and then receive another login code on their mobile phone, email or other device. This code is then entered into the system to successfully complete the login.
In order to protect your business from cyberthreats, multi-factor authentication should be applied to all internet-accessible devices and services, including web and cloud-based email, workplace collaboration apps, virtual private network connections and remote desktop services.
Here’s StormWarden CEO Aaron Harch with some more tips on MFA and cybersecurity.
2. Patch applications
All internet-facing software and apps need to be updated to the latest versions right away. The hackers behind the current threats are exploiting known vulnerabilities for which patches are already available. Updating your software will close known vulnerabilities off from hackers. Reliable app providers are prompt to act and provide ‘patches’ for known threats via software updates, so it’s always best practice to keep install the latest available updates within 48 hours of them becoming available.
3. Patch operating systems
Never use outdated or unsupported versions of your operating systems for your devices. Always ensure your smartphones, tablets and computers are operating with the latest version of their system installed. If a new operating system update arrives, be sure to download and install within 48 hours of it becoming available.
4. Application control
Effective application control will prevent unwanted malware – malicious software – from being able to open and operate on your network. If you have it correctly set up, only approved applications can run on your systems, so even if an employee unwittingly opens or tries to install malicious software, it will do no harm.
5. User application hardening
The ACSC recommends you configure your web browsers to block or better still uninstall Flash, ads and Java script on the internet. It’s also wise to disable any features you don’t need in Microsoft Office (e.g. OLE), web browsers and PDF viewers. That’s because these are popular ways hackers use to get malicious code onto your systems.
6. Block macros
Speaking of Microsoft Office, it’s recommended to configure Office to block macros from the internet. If you only allow vetted macros either in ‘trusted locations’ with limited write access or digitally signed with a trusted certificate you remove the risk of internet macros delivering and executing malicious code on your network.
7. Restrict admin privileges
ACSC describes your operating system and applications’ admin accounts as the ‘keys to the kingdom’ and rightly so! Your admin accounts have the most control and highest levels of access. That’s why it is vital to regularly evaluate the need for privileges and only provide access to those for whom it is essential.
8. Backup daily
Ransomware criminals rely on your need for your own files and data. If successful, they hold this information for ‘ransom’ and demand payment for its release. One way to mitigate risk of becoming prey to these cybercriminals is to conduct regular backups of your software and data files. Your backups should be stored off-site, for example with a reliable cloud storage provider, for at least three months. Some businesses find daily backups to be enough, however if you have a lot of new data applied to your systems throughout the day, it can be prudent to back-up your data even more frequently.
Receive a FREE Security Assessment
StormWarden is offering new customers a free security assessment including dark web scan, internal security audit and one free phishing testing assessment for your staff when you sign up for our MFA cybersecurity services. Download the MFA flyer here or get in touch to find out more about this offer.