In today’s world, everything’s connected. That includes the software your business relies on. Whether you’ve installed that software locally or use it …
Your smartphone is a digital wallet, communication hub, and personal assistant. All rolled into one portable device. It’s packed with sensitive data, …
A business network is the lifeblood of operations. It’s the digital artery that pumps data through your organization. It enables everything from …
Buying a used laptop can be a great way to save money. But it comes with risks. You need to be careful …
The office landscape is undergoing a dramatic transformation. Gone are the days of sterile cubicles and monotonous routines. Today’s smart offices are …
Windows 10 has served us well. But its time is running out. Microsoft plans to end support for Windows 10 on October …
Traveling with technology has become a necessity. Whether for work, communication, or entertainment, we rely heavily on our devices. But traveling exposes …
Imagine this: you walk into your office on a busy Monday morning, ready to tackle the week. But something’s wrong. Computers are …
Running a small business is a whirlwind. You juggle a million tasks and wear countless hats. You also constantly fight the clock. …
Phishing has always been a threat. Now, with AI, it’s more dangerous than ever. Phishing 2.0 is here. It’s smarter, more convincing, …
Is your smart home turning into a smart mess? Do your smart office devices speak different languages? You’re not alone. The current …
The rise of remote work has redefined the modern workplace. Gone are the days of rigid office schedules and commutes. But with …
Gone are the days of paper-laden desks and rows of filing cabinets. The modern office is a hub of innovation. Technology plays …
Artificial intelligence (AI) is rapidly transforming industries. It offers businesses innovative solutions and automation capabilities. But with this progress comes a growing …
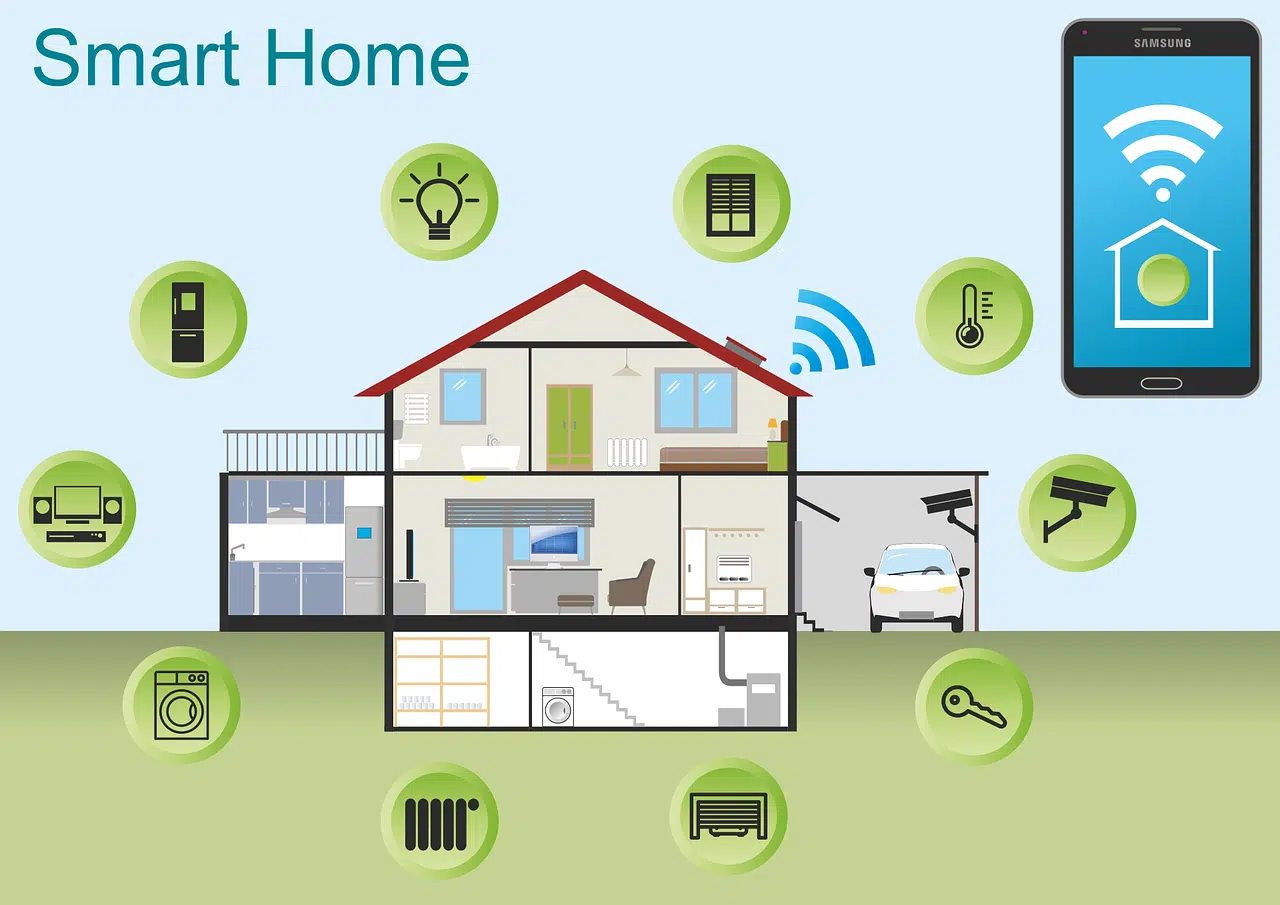
Smart homes seem like something straight out of a sci-fi movie. They have lights that respond to your voice commands and thermostats …
Imagine this: you leave your house for vacation. You live in a shady neighborhood but feel confident your locks are secure, but …
Staying ahead of threats is a challenge for organizations of all sizes. Reported global security incidents grew between February and March of …
Microsoft Copilot has been heading up the business AI charge. It’s used in Word, Excel, Edge, Windows, and more. This genAI-powered app …
Let’s face it, iPhones are amazing devices. But even the sleekest, most powerful iPhone can succumb to the dreaded slowdown. Apps take …
Shiny new tech can be exciting! It promises increased efficiency, happier employees, and a competitive edge. It’s also necessary to stay competitive …
Cyberattacks are a constant threat in today’s digital world. Phishing emails, malware downloads, and data breaches. They can cripple businesses and devastate …
The annual Consumer Electronics Show (CES) was an exciting one this year. It left us with a mind-blowing glimpse into the future …
Imagine a world where your lights turn on automatically as you walk in the door. Your coffee starts brewing before you even …
Data is the lifeblood of modern businesses. It fuels insights, drives decision-making, and ultimately shapes your company’s success. But in today’s information …
Cyber threats are a perpetual reality for business owners. Hackers are constantly innovating. They devise new ways to exploit vulnerabilities in computer …
Zero Trust security is rapidly transforming the cybersecurity landscape. It moves away from traditional perimeter-based security models. In this approach, every connection …
What are some of the key differentiators that can propel small businesses forward? They include efficiency, productivity, and innovation. Microsoft has expanded …
Calendars, task lists, and project planning are important business tools. Many people use Microsoft’s apps to power these processes. Including Planner, Microsoft …
The Internet of Things (IoT) is no longer a futuristic concept. It’s rapidly transforming industries and reshaping how businesses operate. IoT is …
With cyber threats evolving at an alarming pace, staying ahead of the curve is crucial. It’s a must for safeguarding sensitive information. …
Have you been hearing more about email authentication lately? There is a reason for that. It’s the prevalence of phishing as a …
Have you ever seen a video of your favorite celebrity saying something outrageous? Then later, you find out it was completely fabricated? …
Back when you were a kid, living in a “smart home” probably sounded futuristic. Something out of Back to the Future II …
It can be challenging to keep up with the ever-evolving cyber threat landscape. Companies need to process large amounts of data. As …
Cloud computing has revolutionized the way businesses operate. It offers scalability, flexibility, and cost-efficiency. But cloud services also come with a downside: …
We are living in an era dominated by digital connectivity. You can’t overstate the importance of cybersecurity. As technology advances, so do …
QR codes are everywhere these days. You can find them on restaurant menus, flyers, and posters. They’re used both offline and online. …
Smart home devices are becoming more popular and convenient. But they also pose some serious security risks. Hackers can target these devices …
Cybersecurity is a constantly evolving field. There are new threats, technologies, and opportunities emerging every year. As we enter 2024, organizations need …
Microsoft Edge continues to redefine user experiences. This is due to Microsoft’s commitment to innovation. The latest updates bring a host of …
Relentless digital innovation has defined the last few years. The symbiotic relationship between AI and cybersecurity has become pivotal especially when it …
If you employ anyone aged between 16 and 19, you need to pay special attention to the cyber security training you’re giving your team.
Cyber criminals are getting smarter. This recent malware threat is unusually smart. It impersonates a highly trusted brand name to get a foot in the door.
Book now for an IT check-up, to get in great shape for the journey ahead? You do it for yourself and your car – now do the same for your workplace tech
Gen Z and even some Millennial employees are less tech savvy than many employers might expect. It’s an assumption that’s leading to a sense of ‘tech shame’.
Countless employers still don’t trust their people to do their best work unless they’re physically in the office.
With its huge dominance in the workplace, Microsoft’s Windows has become the prime target for cyber criminals.
Passkeys are set to take over from traditional passwords to give us a safer, more secure way of logging into our online accounts.
Almost half of people with social media accounts admit to falling for shopping scams. If your team are shopping at work, is your business protected?
Zoom is looking for a piece of the MS Teams action with the launch of a whole suite of features and services